| Hi, my name is Harry and in this post, I am going to share with you some of what I’ve learned when I took the certification for refreshing my knowledge on Cybersecurity for Critical Urban Infrastructure at MIT which is the best university for Science, Technology, and Engineering. The certification covers the causes and scope of cyber attacks in Critical Urban Infrastructure. This post will also give you some ideas on how agencies can prevent and avoid possible attacks. |

Overview
Critical Urban Infrastructure in cities and states like Energy, Communication, and Transportation are being attacked across countries. Thus, public agencies’ safety will be at risk as hackers encrypt the data causing the different systems NOT to run to provide services. If this happens the hackers will have the leverage to demand ransom for agencies to get their data back. However, paying the ransom WILL NOT give any guarantee that that agency can reuse their data and it is strongly stated to NEVER negotiate and pay the ransom demanded by the attacker/s. In conjunction, it is understandable that the company will negotiate due to the lack of education and expertise and the budget of having a dedicated cyber security team in the first place to prevent it from happening. Lawrence Susskind: Ford Professor of Urban and Environmental Planning, noted that the lack of knowledge can lead to overestimating the cost and complexity of the things that the company can do to strengthen its cybersecurity posture. He also added that an initiative is to use low-cost and best prevention such as “Defensive Social Engineering” to avoid cyber attacks.
Note. As a reference of what is “Social Engineering” and some of the countermeasures, read this pdf slides from Open Worldwide Application Security Project (OWASP): Presentation Social Engineering.
Lines of Cyber Attack (Attack Vector)
People
Technology is a running target and slightly behind from associated updates and misuse can lead to cyber-attacks. Gregory Falco: A MIT Security Researcher who is a Ph.D. within the Department of Urban Studies and Planning (DUSP) and also the founder of the NeuroMesh clearly stated that the number one attack vector or the weakest links are people. This is due to the nature of the business as some people have a special privilege (e.g admin) to different systems, which can be used as an access point for hackers to easily scale the attack once the account has been compromised. Also, without Cyber Security Awareness training for users will drastically weaken the security posture of organizations.
Suppliers
The second is suppliers, this is because most of the companies do not do every part of the product in-house. This is also the reason why there is a supply attack where the supplier entity has been compromised and hacker/s use infected components or parts as a medium to horizontally propagate the attacks to different clients. Thus, can result in an attacker extracting information through the supplier or easily scaling the attack to create huge disruptions to Critical Urban Infrastructure.
Technology
Gregory Falco stated that the most obvious attack vector is the technology itself. Hackers can use Commercial off the shelf Software (COTS) or hardware to exploit and apply these techniques to Critical Urban Infrastructure Systems. Of course, this is because the latter may be using the same software or system for delivering different services. For example, the Windows Operating System can be used by anyone and hackers can try to find different vulnerabilities with the least resistance (low-hanging fruit), to intrude that benefits them the most (balance the cost and rewards). Most likely hackers use existing exploit kits such as Kali Linux which has a different suite of tools that help find different types of vulnerabilities in various systems. The attacker can then also determine if the vulnerability is Zero Day which can be very valuable and can be sold to the black market, which is a huge issue as the vendor might have not created a patch update to clients’ systems.
So what do attackers do once they get to the system? The attacker will persistently stay in the network and may observe for a while. This is also to make sure no one notices the intrusions (stealth assurance) before launching a much bigger attack. This is why people need to be really aware of the different players, types of attackers, the various ways for attackers to get into the systems, and what those attackers do once getting into the systems.
Federal Government’s Response to Cyber Attacks
Danny Weitzner a Principal Research Scientist at MIT CSAIL and a Founder and Director of MIT’s Internet Policy Research Initiative talks about how Federal Government protects America from Cyber-attacks. As a lesson learned from his lecture, I learned that perpetuating a cyber attack is a violation of the law, and the process involved in bringing justice (e.g. maybe to capture the attacker) with the help of law enforcement is a little bit more complicated. This makes sense because a careful attacker can disguise their identity, IP address, and locations using encrypted communications which can be very hard to track them down. What even makes it harder is the fact that the behavior of the attack came from a state-sponsored hacking group which makes it even harder to arrest the criminals.
Computer Fraud and Abuse Act (Main Law – 1986)
The CFAA law does two things, 1) it is a crime to use a computer without authorization. This means that even if the password is clearly written on the sticky note on that person’s desk, you as another user cannot use it, to access that person’s computer account. 2) The CFAA also makes crime to exceed your authorized access to a computer. This means you should only access the ones that the organization/company permitted you to, for successfully doing your job. So, violating any of these hacking laws will lead to a very stiff penalty or 1-20 years of sentence in jail (conviction) time. In addition, some of the big agencies that enforce these laws include but are not limited to the United States Federal Bureau of Investigation (FBI), the United States Department of Homeland Security (DHS), and the United States Secret Service (USSS).
While seemingly the U.S has a strong law in place in regard to protecting America from cyber-attacks and prosecuting criminals, Danny makes it clear that in the 2018 cyber security attack incidents, there is only less than 1% actually led to arrests and fewer that led to convictions. This is hugely out of proportion as there is 300,000 incidents that were brought to federal agencies’ attention. He also added that while we have agencies such as Central Intelligence Agencies (CIA) and National Security Agency (NSA), they are very sophisticated about cybersecurity issues, and do not have a mission to protect individuals or private sector organizations.
Cybersecurity and Infrastructure Security Agency (CISA)
U.S Department of Homeland Security Agency’s main objective is to enforce private sector organizations to use good cybersecurity practices and learn any information about incoming threats. DHS focuses on these 16 Critical infrastructures that the functions of society heavily depend on. As Danny (04/2024), said “These are the things without which our society can’t really function.”
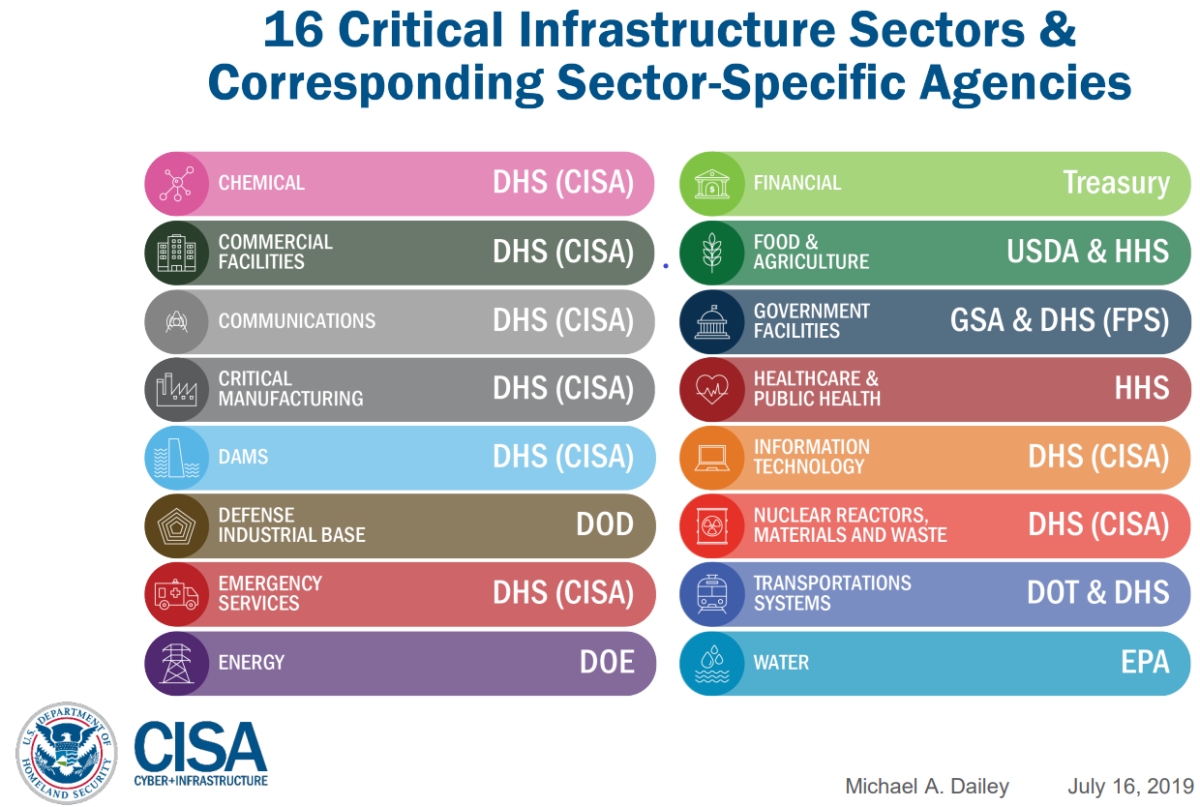
Note. Image barrowed from web (CISA Regional Service Delivery Model)
The DHS also organized the Information Sharing and Analysis Center which is a voluntary gathering place for entities associated with these 16 sectors. DHS coordinated to make sure all of these sectors are sharing what kind of threats they are encountering and sharing the best cybersecurity practices to protect the organizations against those threats.
Furthermore, there are also the Government Coordinating Councils, a collaboration between the state and local government agencies to share information similar to the aforementioned. And lastly, DHS has the Science and Technology to fund research and advance development for cybersecurity to benefit the U.S. in the long run.
Defensive Cybersecurity Practices
Danny Weitzner mentioned in the lecture that one of the key things is that “there an asymmetry between the adversaries and those who they attack” Danny (04/2024). As an analogy, the organization should have strong security in place and be ready for any attack that may come from different ways. The federal agencies encourage organizations to follow the best practices using the framework provided by the National Institute of Standards and Technology (NIST). NIST agency has been around for more than 100 years composed of scientists and engineers and its primary goal is to create process standards. However, NIST does not make decisions, for example, prescribing what encryption algorithm should be used or what hardware you should be building, but rather NIST creates a set of questions to ask concerning e.g cybersecurity posture and being aware of ways in which an organization is prepared and ways which could be improved, Danny (04/2024).
To read more about the NIST Cyber Security Framework, please visit Framework for Improving Critical Infrastructure Cybersecurity, Version 1.1 (nist.gov).
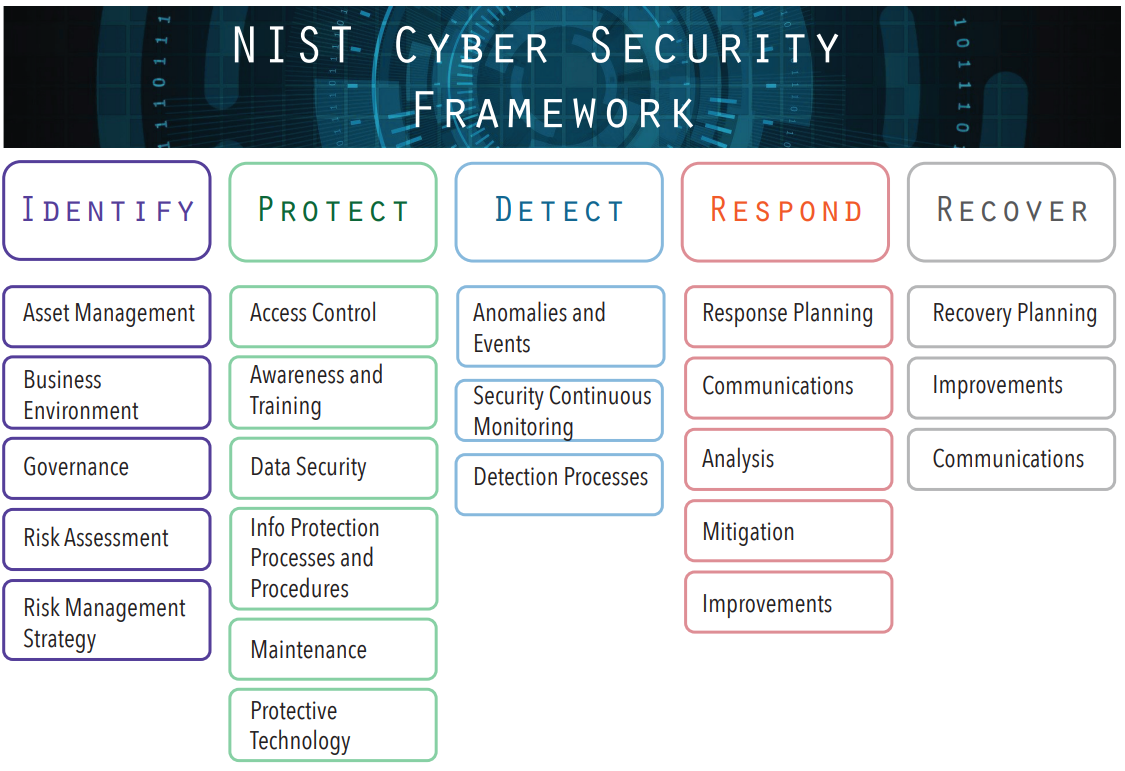
Note. Image barrowed from web (NISTFramework (mit.edu))
Who Are The Attackers Exactly?
As you probably know, attackers have only one goal in mind, to infiltrate the system. However, attackers involved in Critical Urban Infrastructure are often nation-states. This attacker may be interested in money but the biggest goal is to disrupt what makes society function. When a Critical Urban Infrastructure System stops, some of the entities or processes associated with it will not be able to function which puts public safety at risk. Gregory Falco gave the previous SamSam Ransomware attack as an example. The ransomware infects the Windows Server that Critical Urban Infrastructure uses then propagates to different networks and takes down a series of transits. So that said, the ransomware didn’t solicit money but wanted to cause chaos and a state of emergency, Gregory Falco (04/2024).
Another one is the Baltimore Ransomware Cyber Attack (“Robbinhood” ransomware). The City of Baltimore in Maryland experienced a sequence of cyber attacks that the 911 and 311 dispatchers departments had to switch to manual processes due to inaccessible computers. This attack put the people at risk as the city will not be able to access the data in their system to provide service to the community. What was dangerous during this ransomware attack was that the city was not able to pinpoint when it would be back online which also led people to endure. The attack also causes the city to spend $20 million for the remediation effort for rebuilding computers, data recovery, and loss or deferred revenues.
Key Takeaways
- Cyber Attacks are increasing to Critical Urban Infrastructure.
- The federal government takes responsibility for protecting America’s defense establishment, including all of its suppliers from cyber-attacks.
- Different line of attack (attack vector) can occur and involved a wide range of attack mechanism.
- Ransomware continually leverages the amount of money that they are demanding to release the data held hostage.
- Some cyber-attacks that happen in Critical Urban Infrastructure have been traced back to foreign individuals or entities (countries).
- Case studies such as the Baltimore Ransomware Cyber Attack show how can a city be brought to a halt that puts public safety in danger.
- Company can adapt Defensive Social Engineering and do a vulnerability assessment to strengthen its cyber security posture.
Conclusion
As for this post, you should now have a good idea of what is considered Critical Urban Infrastructure, the different lines of attack (Attack vectors), and the different laws and best practices that the U.S. created to protect America from different cyber attacks. Hope you enjoyed this post, please subscribe as there are definitely more updates to come.
References
Baltimore Cyber Attack (2019). Retrieved from https://en.wikipedia.org/wiki/2019_Baltimore_ransomware_attack
Cybersecurity for Critical Urban Infrastructure (08/2024). Retrieved from https://mitxonline.mit.edu/courses/course-v1:MITxT+11.S198x/