In this post, we will see how to test any SSH server for the so-called “Terrapin” which is a cryptographic attack on the SSH server & client during key handshake negotiations. Note that the latter is defined as “RFC8308” which is a mechanism for Secure Shell (SSH) clients and servers to exchange information about supported protocol extensions confidentially after SSH key exchange (www.rfc-editor.org, March 2018). Before the vulnerability release, the strict key exchange was not supported by the SSH server which is a big flaw as Man-In-The-Middle can use this to mimic the negotiation to the server (and vice-versa). Thus, will not be noticeable to both the client and server. The following image shows how the Man In The Middle can call the EXIT_INFO and inject INGNORE packets to the client to avoid possible detections.
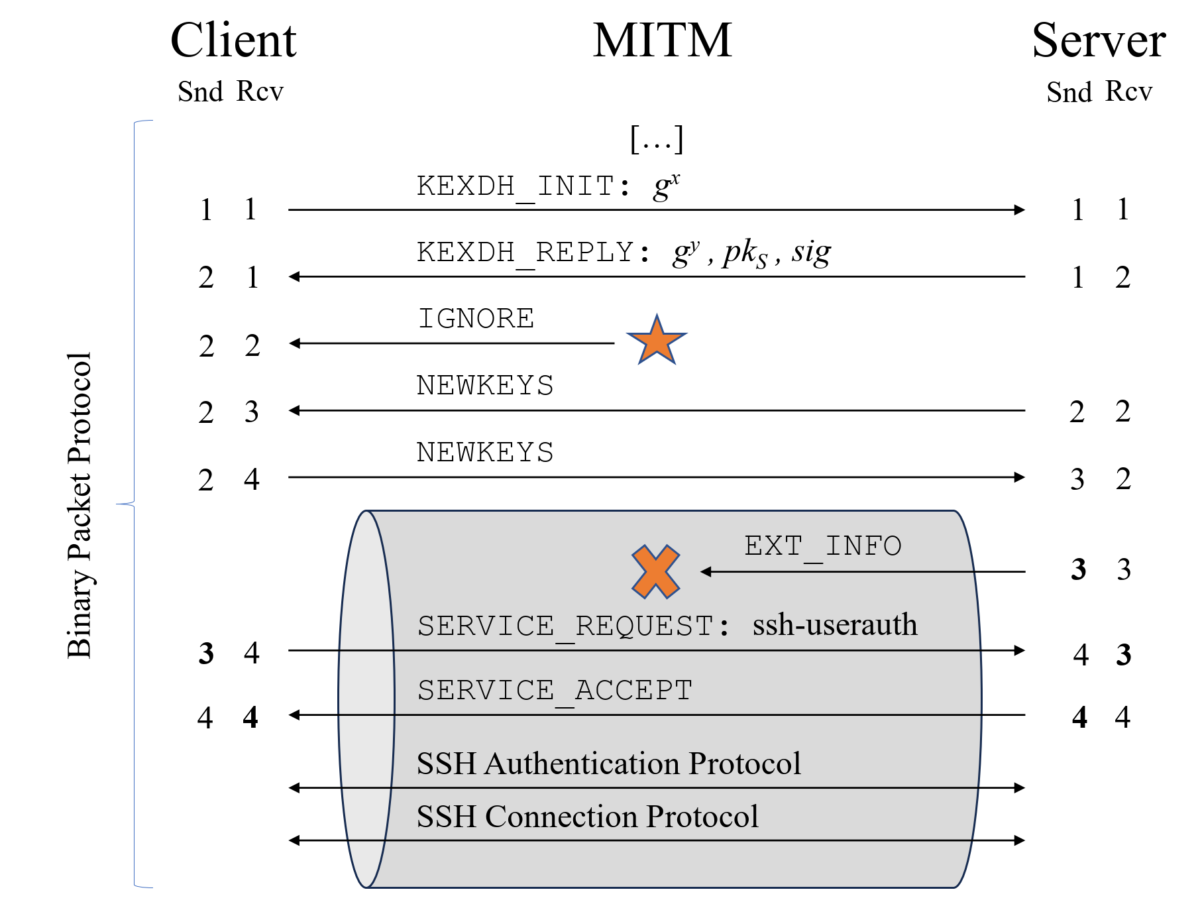
Note. Image is borrowed from website Terrapin Attack (terrapin-attack.com).
As consequences, during the key negotiation the attacker can downgrade the connection to less secure and bypass the underlying authentication mechanism that implemented in the ssh/application using ssh library. Therefore, attacker can easily perform a vertical privilege escalation to do Remote Code Executions (RCEs) or use the account machine to send phishing emails at a very least. So, if this happens, it is common sense already to what the attacker can gain from you network.
While the above information is not a complete detail on how the attack works and what are the different functions of each sequence, the goal of this post is to show what tool we can use to test/scan the server for this SSH vulnerability. Fortunately, there is a repository given by Terrapin-attack.com to determine if the server or client is vulnerable. This will scan the server and check the vulnerable key exchange extensions such as ChaCha20-Poly1305 or CBC with Encrypt-then-MAC encryption modes.
Terrapin Scanner
Thankfully, the terrapin-attack.com website created a repository with the compiled tool for different operating systems environments to test whether SSH is vulnerable.
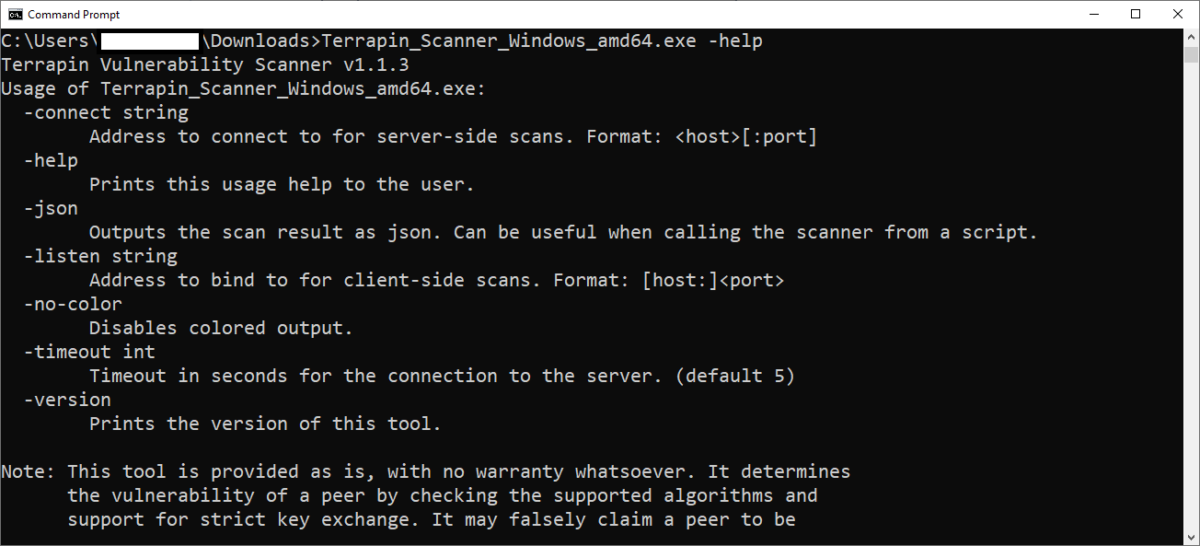
Note. Download the terrapin scanner at https://github.com/RUB-NDS/Terrapin-Scanner/releases/tag/v1.1.3.
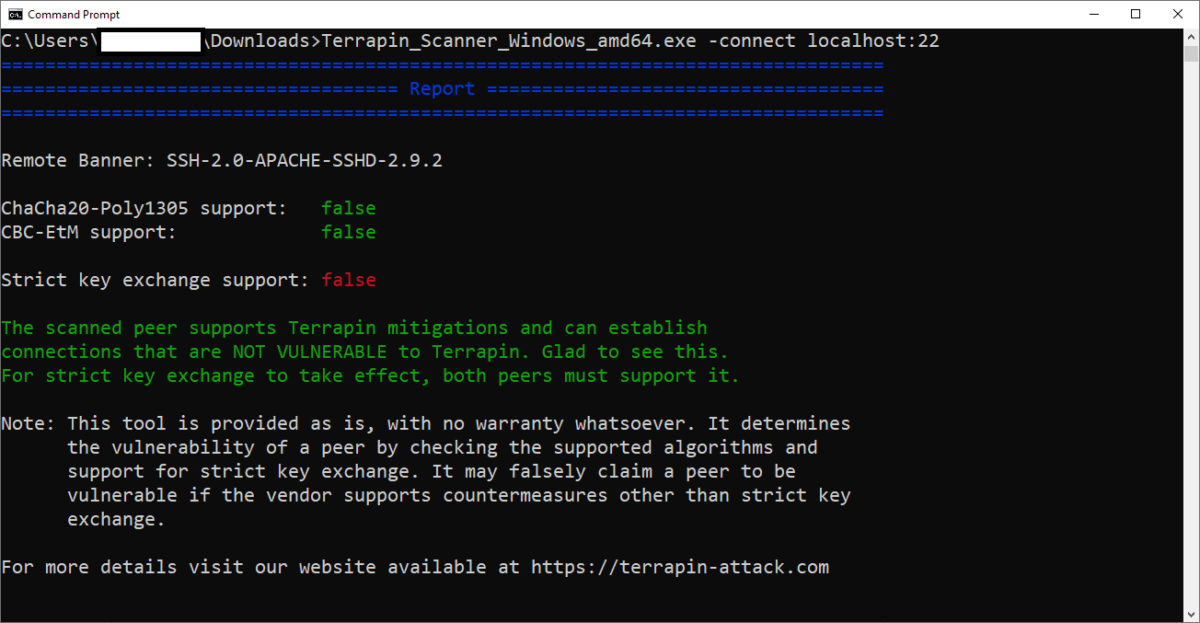
The command that needed to test the server is “-connect host[server/ip]:port”
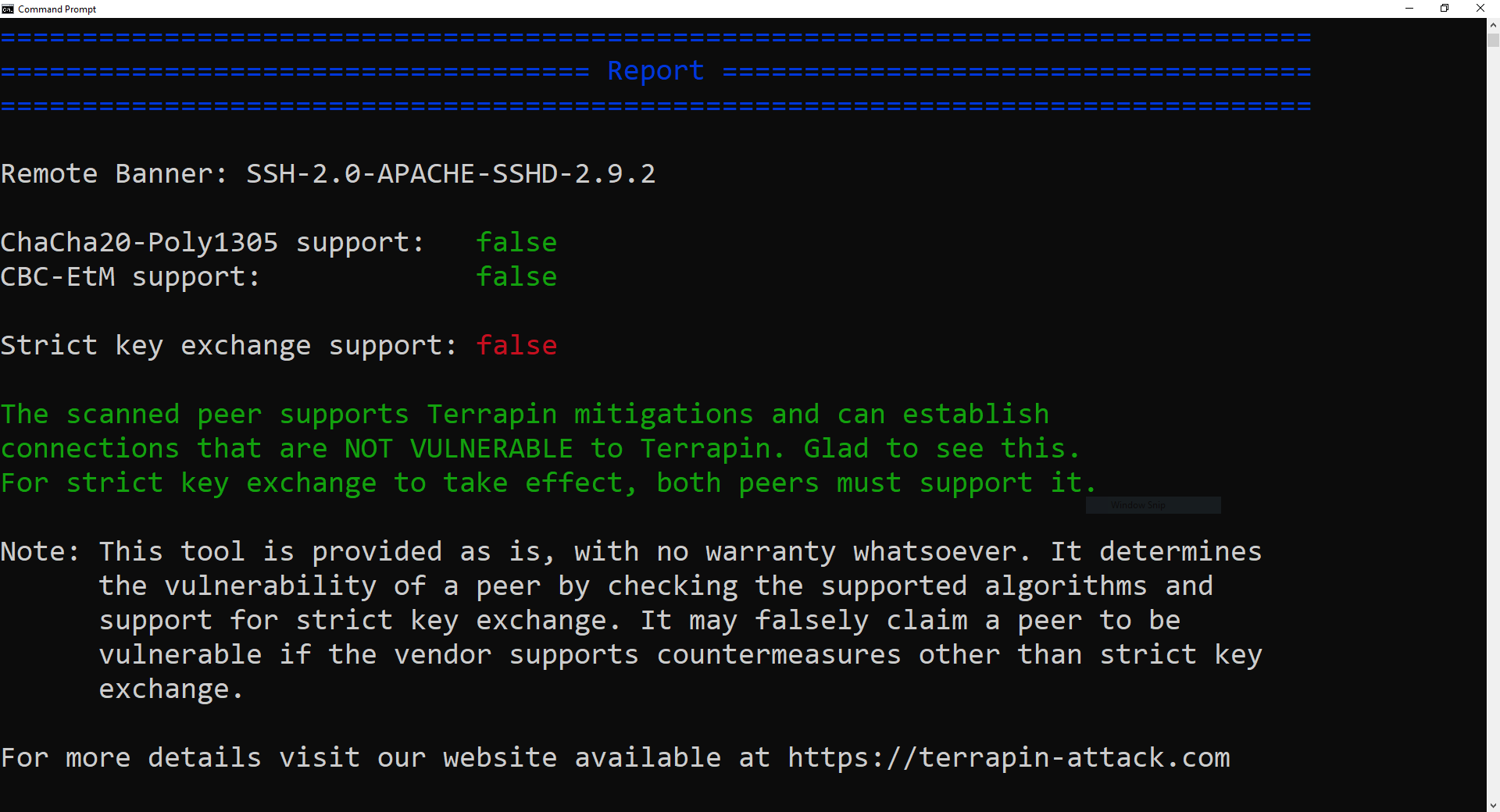
For example, if you run the SFTP Server/SSH Server and execute and scan with the said command, if it gives the following result, this means that the ChaCha20-Poly1305 or CBC with Encrypt-then-MAC encryption algorithm is not supported. This means that the server is not vulnerable as it does not apply the said extensions. However, the critical here is the Strick Key Exchange Support is not implemented by the server. This also means that if one or two of the algorithms is supported in the server the Strick Key Exchange Support should be set to true (Implemented) in the server. Note that both the server and the client should support this as the adversaries can use any of these as the entry point to attack the channel (as these are bilateral).
Note. To read more about the terrapin, please visit https://terrapin-attack.com/.
Verdict
This type of attack urges the requirements of having Man-In-The-Middle to exploit the channel and this can be very difficult to do over the internet. However, it still depends on how strong the security measure of the organization is to exclude unknown hosts (or in applying a demilitarized zone a.k.a DMZ). If the adversary is somehow connected to the local network then this is a plausible attack. That said, it is always recommended to apply the different countermeasures or to apply any updates as prevention for this said key exchange vulnerability. So, that said, start scanning your ssh server now using the pre-compiled tool given by Terrapin Attack (terrapin-attack.com).