Who is the Target Audience?
- You are concerned about hackers, cyber-criminals, malware, and viruses.
- You want to keep communication and personal information private.
- You are a business owner and want to protect your assets, business information from any adversaries/competitors.
- Anyone who has an interest in security, privacy, and anonymity.
Subjects
- Who are the adversaries?
- What might be the threats?
- Why Hackers Hack?
- Determine what you value; and
- How to protect it.
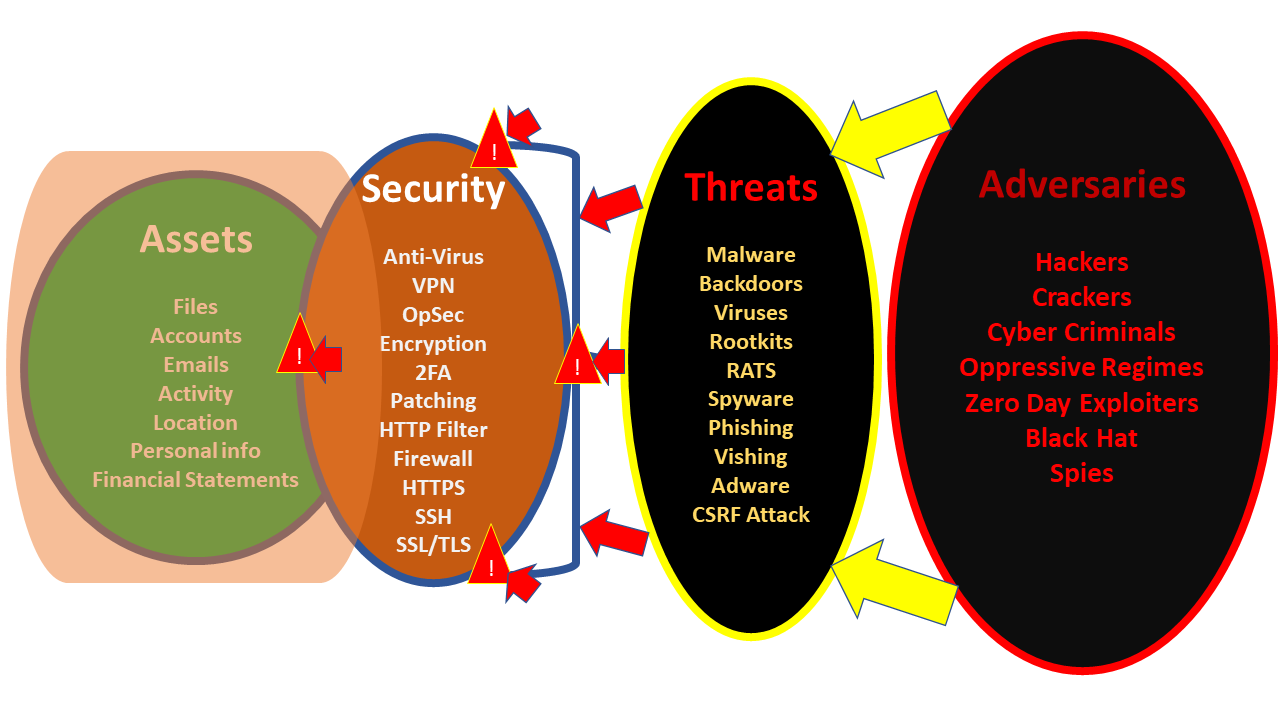
Who are the adversaries?
Adversaries could be anyone that has bad intentions. These might be a group of hackers, cybercriminals, and could be spies that want to learn about the company’s business flaws in order to bring it down (Perhaps Competitors). Read the “The Dark Side of Business Competition” posted by Kelly Richardson. Good competitors make you think creatively in a matter of improving your business but bad competitors will not.
Adversaries are not necessary at the same location as your business is. Any individual or group that has a good fund from a known or unknown source can initiate an attack on to any individual or any business.
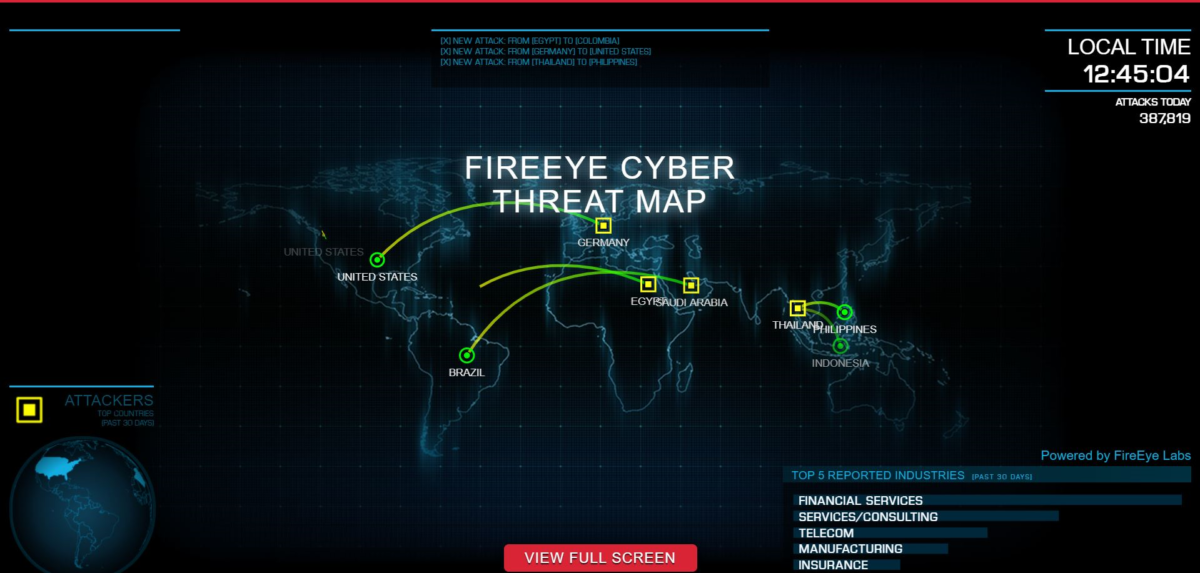
See the Live Cyber Threat Map
What might be the threats from Adversaries?
In the modern tech world. Threats are could be any form of programs that made from adversaries or groups of tech-savvies that will do anything to get something upon intrusion. A potential intruder can initiate the attack by a virus or malware. Let’s say you downloaded a piece of software called “Antivirus For Free” from an unknown website. Cool, it is free and you installed it on your computer.
What you installed is basically Malicious Software (Malware) and this malware may open a backdoor to bypass all your securities. The backdoor can be used by the hacker to take over the whole device’s systems and will spread using your network connections. YES!!! it is very creepy…
Viruses/malware are made of a series of codes that follow steps of algorithms, this can be really dangerous unless it is a directed attack that only looking for something very specific configuration. i.e the Stuxnet virus that launches in Iran to destroy nuclear centrifuges. Stuxnet virus is made only to attack Iran’s nuclear plant PLC configurations in order to delay and destroy its nuclear development.
In the case of the Stuxnet virus, the nuclear plant configuration is something that individuals can not have inhouse. Otherwise, if you have the target latter then you should worry if this virus gets on you…
Why Hackers Hack?
Four primary motives have been proposed as possibilities for why hackers attempt to break into computers and networks. First, there is a criminal financial gain to be had when hacking systems with the specific purpose of stealing credit card numbers or manipulating banking systems. Second, many hackers thrive off of increasing their reputation within the hacker subculture and will leave their handles on websites they defaced or leave some other evidence as proof that they were involved in a specific hack. Third, corporate espionage allows companies to acquire information on products or services that can be stolen or used as leverage within the marketplace. And fourth, state-sponsored attacks provide nation states with both wartime and intelligence collection options conducted on, in, or through cyberspace.
Source Wikipedia
Determine what you Value
Example of Assets you need to SECURE
- Credit card details
- Bank account details
- Primary/Main Email
- Password Information
- Financial records
- Social media information – LinkedIn, Facebook, Paypal, Instagram & etc..
The aim is to assess and determine what you value the most. To apply security, at least know the following:
- What is most confidential?
- What you do not want to lose?
- What is irreplaceable?
- What causes the most damage?
- What impacts your reputation?
Knowing these are a good baseline in order to determine what security controls you must implement to your business. A good and crystal clear assessment will help you a lot for what are the security attributes you need in detail.
Good security implementation can have a big positive impact on you or with your business organization. Though, there is no such as 100% perfectly secured. If anyone claims for securing your information 100% then I can guarantee that person doesn’t know what he/she talking about.
How to PROTECT your Assets
The following are the basic few things and tips I want to pinpoint to prevent cyber criminals to get into your computer, social media accounts and to your business.
See how can we slow down or even pissed off hackers from keep trying until they’d give up.
- Apply Operating System updates – Computer OS updates are very important. Make sure that you scheduled at least weekly automatic updates. If you are using your computer more frequently (every day) then I recommend setting it to auto-update. Enabling this will give you more security for bug fixes in the operating system(OS) that the developers found before cybercriminals/hackers figure it out.
- Install Antivirus – Make sure to get a reliable Antivirus. Installing “Good” Antivirus to your computer and keep it updated is almost impossible for malicious software (Malware) to act. Antivirus will scan your files and programs. If anything acts suspiciously then it will be blocked, quarantined, or even deleted automatically. See Top 10 Antivirus. Also, note that you can use the default Windows 10 free antivirus if you do not want to buy one.
- Only Use Secured Networks – Connect only to a Secured Network. If you connect to any open network i.e in the GYM/Coffee shops then you are exposing your machine/computers to others. You might not notice that someone already tricked you to connect to a compromised network. If you connected to it then all the traffics (Data/Information) between your computer through that network is exposed.
- Use Strong Password – Passwords aren’t necessarily long but must be complex. Remembering long/complex passwords can be difficult and frustrating. Well, the good news is, there are Password Managers out there like StickyPassword. Using such as the latter, you can store all your credentials in one place. StickyPassword can also login you in automatically so that you don’t have to ticked the unsecured “Remember my Password/Login” in any of your accounts next time.
Is that all you can do to secure your computer?
Actually no, but what I’ve mentioned above is a strong foundation and gives you a rich idea of how to secure yourself or your organization’s IT equipment. If you need more info don’t hesitate to Contact Us.