In this post, we will discuss the Resource Consumption Attack that can be initiated by Denial of Service (DoS) for exploitation. This is a software bug or software inefficiency to handle multiple tasks that may lead to resource memory disruption. This common problem is also referred to as a memory leak that can be caused by an infinite loop, mass heavy cryptographic request via the application programming interface(API). An example interface is in the authentication aspect of the application to which users can be granted to access resources. Thus, if the request is more than the server memory can handle (Threshold) then this may cause a serious problem within the application and may share the resources that are not supposed to be.
The Adversaries
Never underestimate the adversaries, despite the motivations, the individual can create a more sophisticated attack with the help of a botnet. Thus, can form Distributed Denial of Service (DDoS) in which constructed network group overwhelmed the same target. It is worth mentioning that the Cloudflare post “Cloudflare thwarts 17.2M rps DDoS attack — the largest ever reported” a new botnet that ever break a record for sending a bogus 17.2M request per second. Note that if your network and software that uses your internal resources which are also exposed to the internet isn’t capable of handling this type of mass request then this can be very dangerously escalated.
In this sense, if your internal network is overwhelmed by this type of attack then the adversaries can inject any payload (script) into the malfunctioning system due to a lack of resources and divert any events processes executions.
Common Target Functions
While every company usually has its own system administrator for securing network IT infrastructure, this will not stop any brute force attack on such application (software) that is exposed outside the company’s premises. For example, any solutions that serve resources to be accessed by the third-party company that might be part of Electronic Data Interchange. Adversaries have a keen eye for exploring software vulnerabilities that have never been discovered before( A.K.A Zero-Day vulnerability).
Sometimes, these sophisticated individuals love to iterate massive parallel requests to the application level, for the purpose of trying to reveal malfunctioning space from the system flow and then use this to gain access. Let’s see in the following figure (see figure 1) how the server (computer) run out of memory due to mass request under the CPU memory level using the vulnerable application.
Behind the Scene During Memory Consumption
A quick view of where all the instructions happen stored, this is called the Stack or you can call it a container of the stack frame. This stack frame contains the method parameters, return address, and local variables involved in the instructions as a whole by any event request. So in this sense and if the stack is continually filled out by multiple stackframes due to recursive calls then eventually the stack will be full and this will cause stack overflow exceptions.
Figure 1
Stack Memory
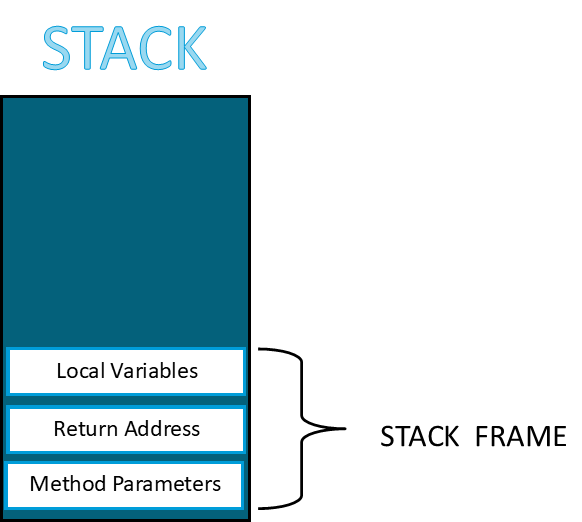
Note: When a Stack overflow happens then this may put the application in an unstable state if this situation is not handled carefully. So with that said, given the latter were true, this complements the resource exhaustion attacks if bad software design practices were used and if the server met the thresholds of handling requests in the stack.
Figure 2
Heap Memory
Another type of memory in the CPU of the computer is the “Heap” which allocates objects. Anything in the heap refers to the stack. In the following figure, you can see the collection of items in the List assigned in the new object then extract the list items in the heap. There is no specific name of the list in this example as this can be a list of anything you can imagine such as a list of users and etc... The critical to understand here is when the stack is deallocated the objects in the heap continue to exist which will be checked by the garbage collection (GC) periodically. The garbage collection process for cleaning the heap memory can take a lot of time and that’s why this may not happen immediately during deallocations.
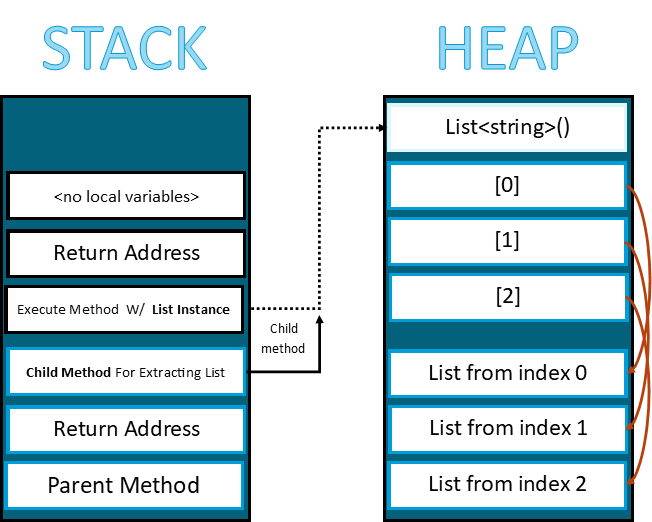
Note: In computer programs, any new keyword will create an object in the heap. When a heap overflow occurred, and since all related objects in the application happen during runtime (when the application is being used), the data can be corrupted as reference objects may not be mapped (point) correctly. This means that the destination address (pointer) for the desired result may receive incomplete or wrong data which disrupts other processes in the application. Also, note the heap memory overflow is exploitable, and the attacker can extract the application data if it finds the right offset to where the data is stored.
So, if both Stack and the Heap are hammered by an attacker in the network by sending massive requests instances. The Computer’s Central Processing Unit (CPU) memory might not be able to process all due to its parallel busyness, which then brings it to timing process vulnerability. You can read or explore more about the Process timing logic vulnerabilities on the OWASP website.
Consequences Scenario in SSH & SFTP Server
By default, SSH FTP does not have built-in security attributes to determine the legitimate user based on the geographical manner and IP address. It also does not have a good prevention of limiting sessions and connections for the users who want to access the remote resources from the server. Thus, can overwhelm the application that processes the request resulting in the memory resources being consumed. As mentioned, if the latter happens, your server may be disrupted and might be brought to an intermittent halt that will not be able to process necessary tasks in order correctly.
In addition, if an unauthorized user is able to find the undesirable malfunctioning function or bug of the system, this can allow the attacker to perform Remote Code Execution (RCE) as an attack surface within your network to steal data.
Attack Escalation Preventive Measures
All professionals would agree that there is no such thing as 100% security. Looking to the big picture on how to handle the resource consumptions attack is to use the best security practices within your organization. In addition, it is good to note that only use good technology products, well-maintained software (even if lightly expensive), and only work with trusted software vendors. From the SSH FTP/SFTP server perspective, there is some software that acts like a wrapper that uses SSH FTP protocol to control the different security control such as IP Filtering, Automated Banning, Thresholding users, control sessions, and limiting failed attempts.
In addition, limit the parallelism of the allowed user’s authentication negotiation and disconnect the exceeding sessions immediately if the thresholds number is reached. Also, monitor the active session and remove the ones that are not currently in use (Inactive).
Conclusion
This post only gives you a basic understanding of what a “Resource Consumption Attack” is in the SSH FTP/SFTP Server. Also when dealing with such servers, it is your responsibility to use the best security practices within your organization in terms of implementing different security controls and their attributes. As a disclaimer to this post, PORTA SFTP SERVER also create a new wrapper application SSH/SFTP called Porta SFTP Server that has the capability to secure credentials and implements the mentioned security above to protect your resources.
There are also other options which can be located here https://www.comparitech.com/net-admin/best-free-sftp-ftps-servers/
References
OWASP(2022). Test for Process Timing. Retrieved from https://owasp.org/www-project-web-security-testing-guide/latest/4-Web_Application_Security_Testing/10-Business_Logic_Testing/04-Test_for_Process_Timing
Udi Ben-Porat, & et al (May 2008). Vulnerability of Network Mechanisms to Sophisticated DDoS Attacks. Retrieved from https://www.researchgate.net/publication/224311569
Omer Yoachimik (Aug 2019). Cloudflare thwarts 17.2M rps DDoS attack — the largest ever reported. Retrieved from https://blog.cloudflare.com/cloudflare-thwarts-17-2m-rps-ddos-attack-the-largest-ever-reported/
Cwe.mitre.org (2009). Uncontrolled Resource Consumption. Retrieved from https://cwe.mitre.org/data/definitions/400.html